Install Aerospike Kubernetes Operator on Red Hat OpenShift
Aerospike Kubernetes Operator (AKO) is a RedHat Marketplace certified operator. It is available through the RedHat certified operators catalog.
Install AKO
You can install AKO on your OpenShift cluster using any of the following methods:
This is the procedure to install AKO on Red Hat OpenShift using the web console.
-
Launch the OpenShift web console.
-
Using the
Administratorview, navigate toOperators>OperatorHub. -
Search for
Aerospike. -
Select the
Marketplaceversion of the Aerospike Kubernetes Operator as shown in the following image.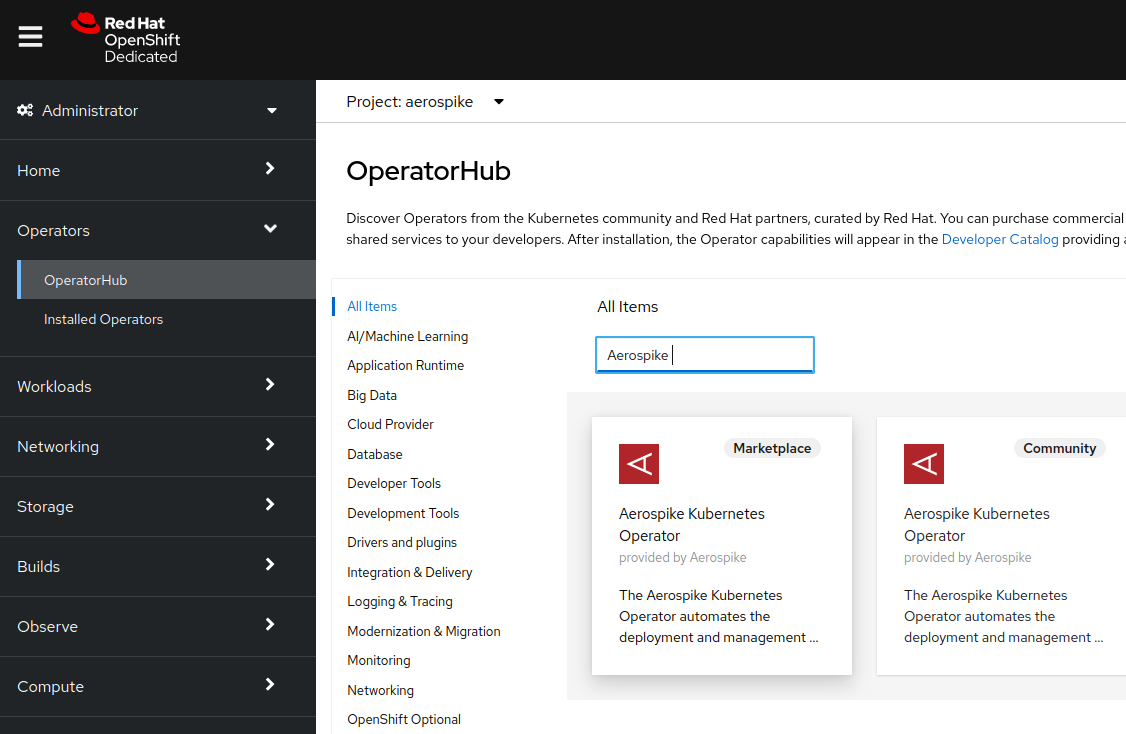
-
A dialog appears describing AKO as shown in the following image. Click
Installto install AKO.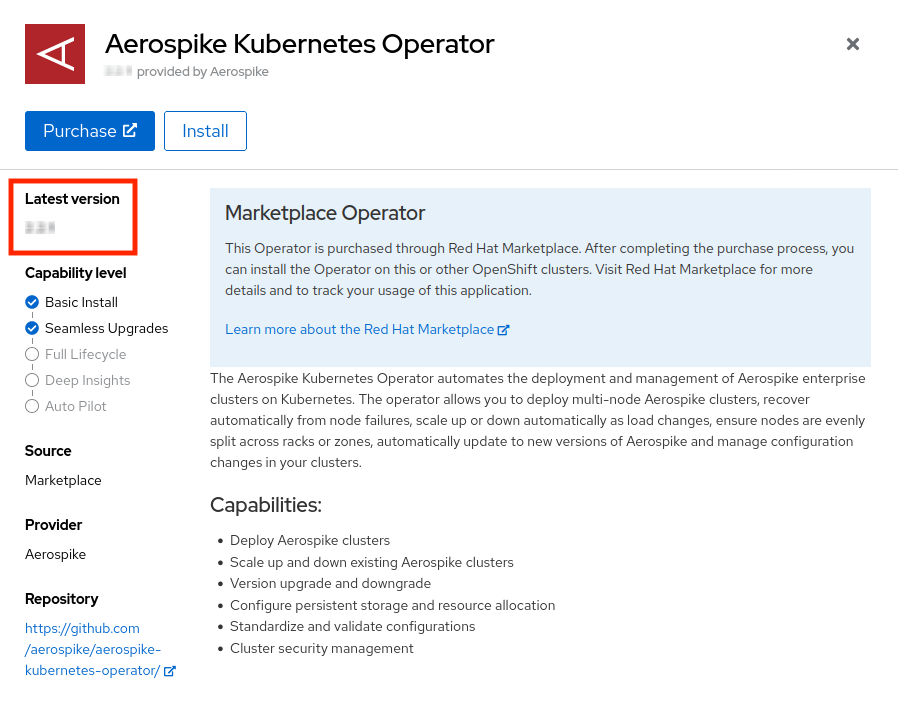
-
Configure AKO installation using the following image as an example.
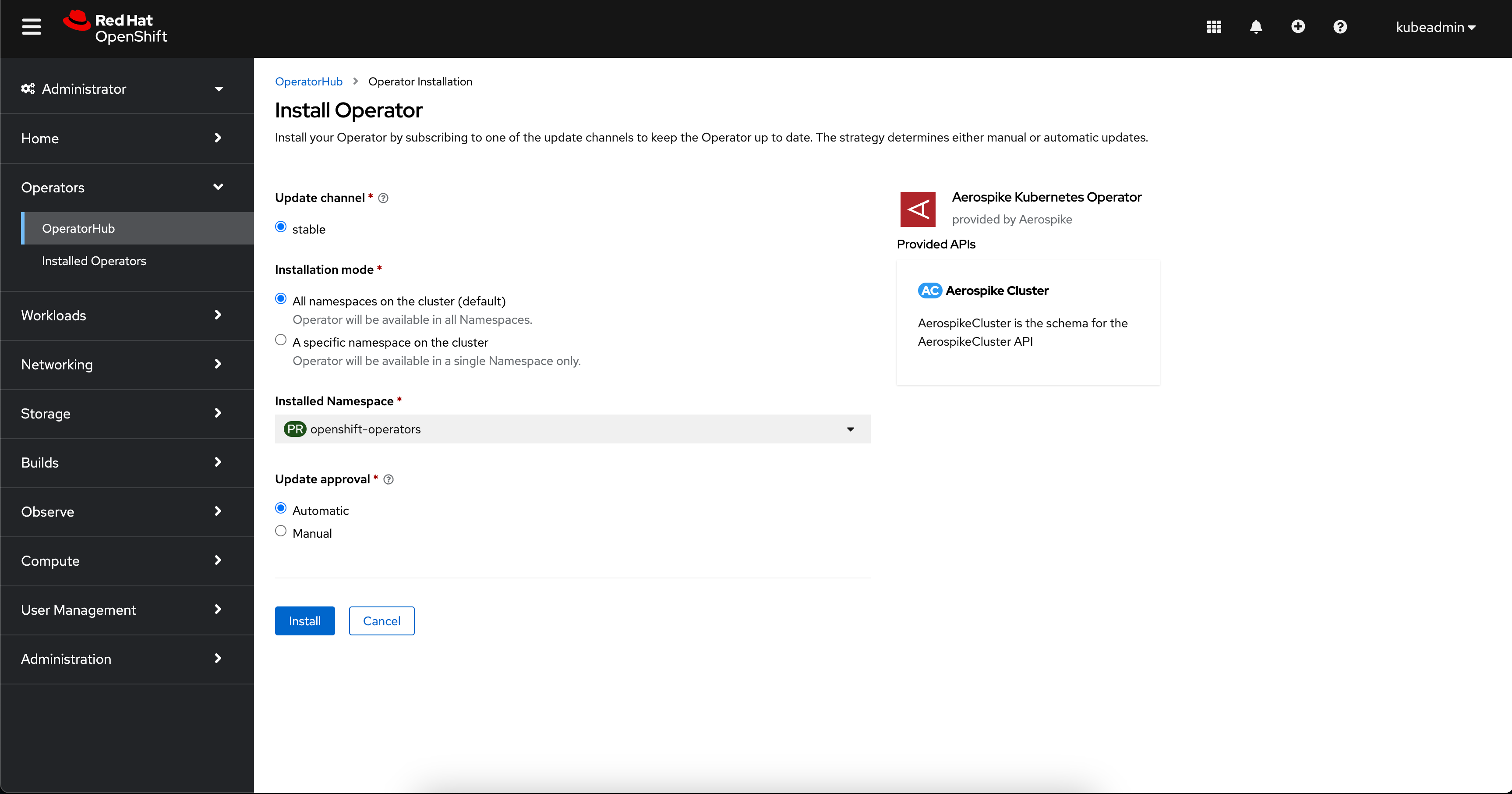
-
Select
openshift-operatorsas the namespace. -
Select
AutomaticforUpgrade Approvalto automatically upgrade AKO whenever upgrades are available.After a successful installation, a message similar to the following appears.
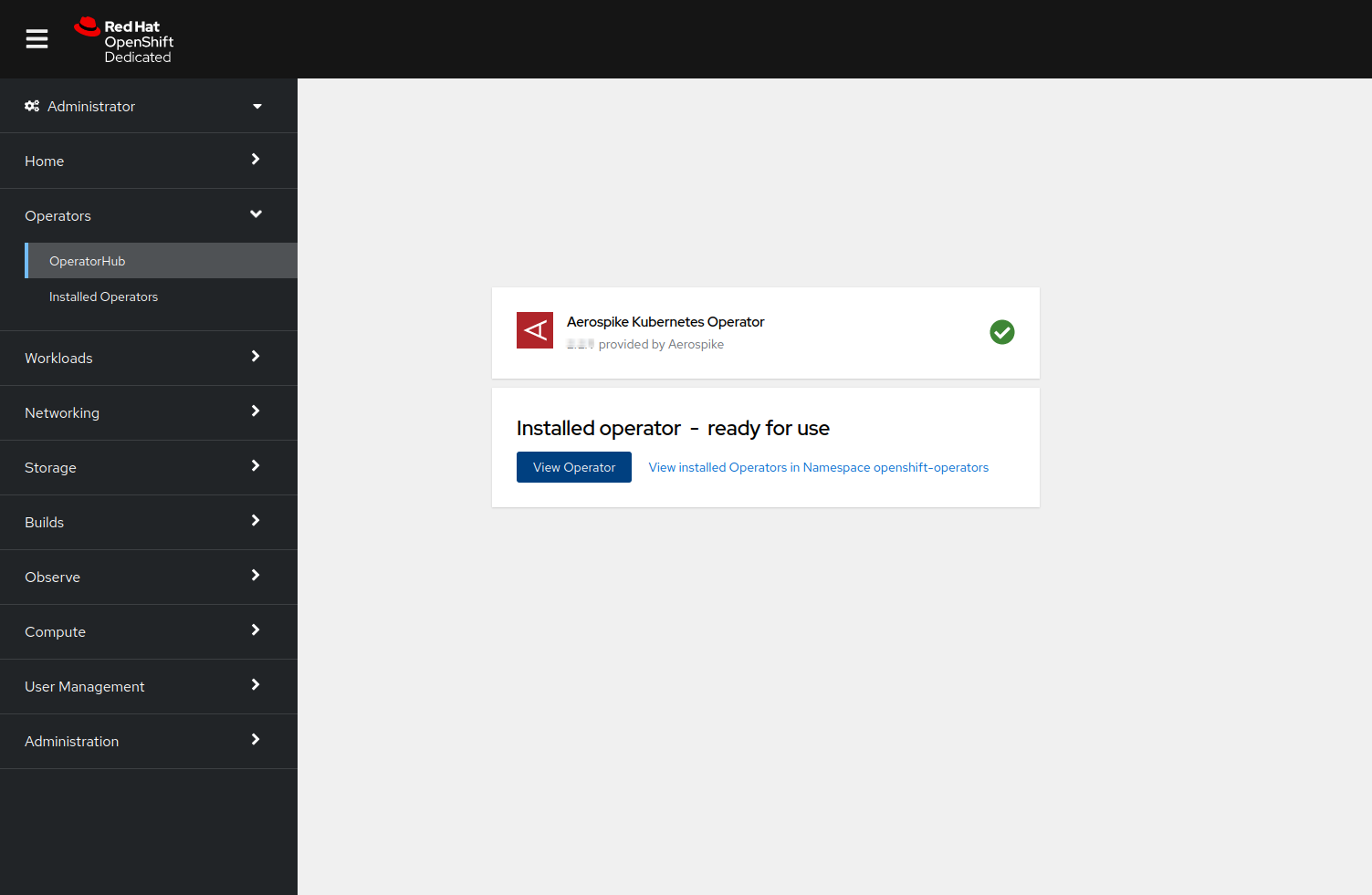
-
Select
View Operatorto verify the AKO details. The details should be similar to the following example: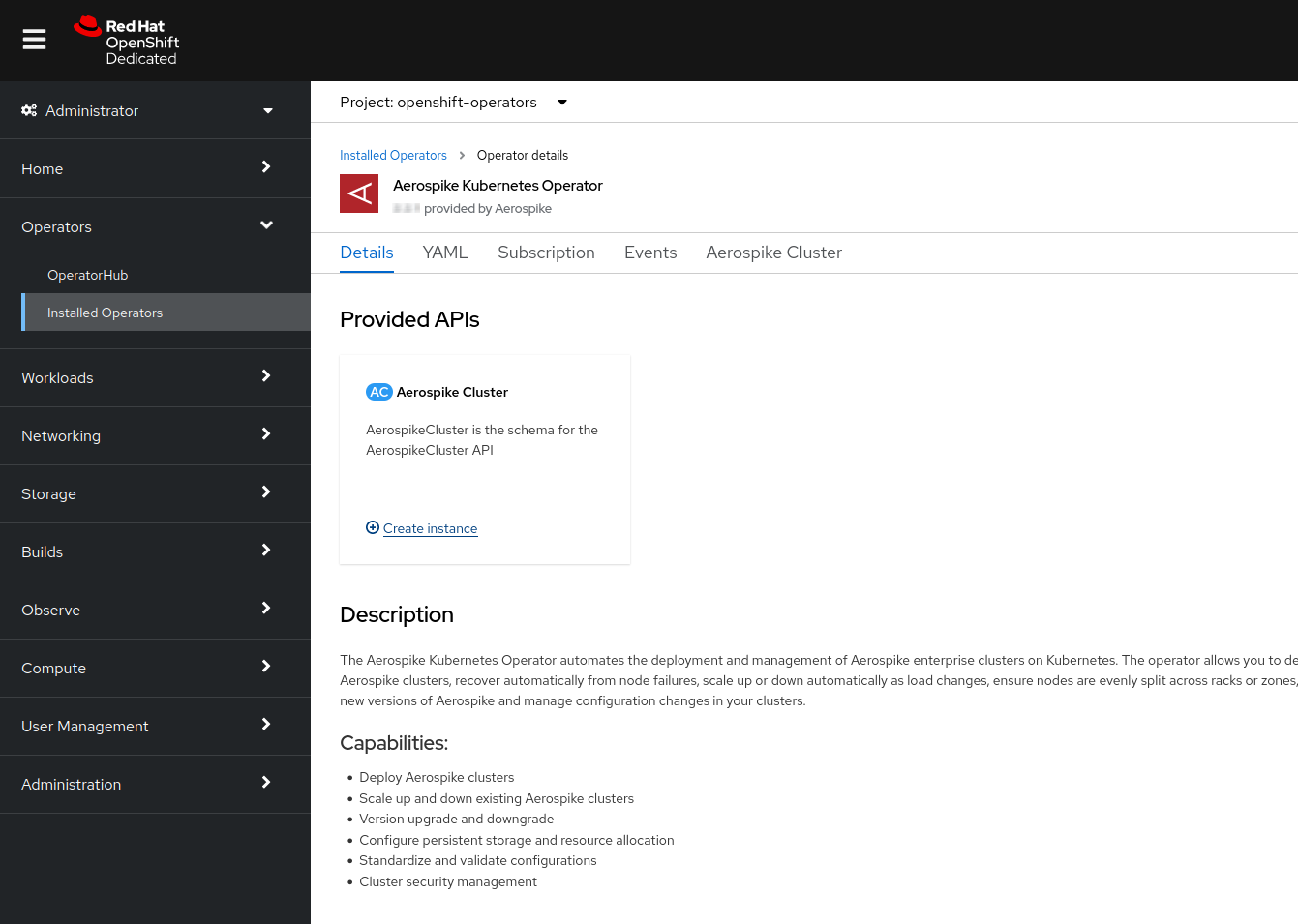
-
From a terminal, log in to the OpenShift cluster and ensure that the
ocandkubectlcommands connect to the correct OpenShift cluster.
This is the procedure to install AKO on Red Hat OpenShift using the command line tools.
-
From a terminal, log in to the OpenShift cluster and ensure that the
ocandkubectlcommands connect to the correct OpenShift cluster. -
Ensure the AKO package is visible by running the following command.
Terminal window kubectl get packagemanifests aerospike-kubernetes-operator-rhmp -n openshift-marketplaceOutput Terminal window NAME CATALOG AGEaerospike-kubernetes-operator-rhmp Red Hat Marketplace 22d -
Create a subscription file
aerospike-kubernetes-operator.yamlwith the following contents:apiVersion: operators.coreos.com/v1alpha1kind: Subscriptionmetadata:name: aerospike-kubernetes-operator-rhmpnamespace: openshift-operatorsspec:channel: stableinstallPlanApproval: Automatic #Automatically upgrades AKO whenever upgrades are availablename: aerospike-kubernetes-operator-rhmpsource: redhat-marketplacesourceNamespace: openshift-marketplacestartingCSV: aerospike-kubernetes-operator-rhmp.v{{version}} -
Create this subscription using the following command:
Terminal window kubectl apply -f aerospike-kubernetes-operator.yaml -
Wait about 20 seconds for the install process to begin.
-
Verify that AKO’s CSV is in the
Succeededphase with the following command:Terminal window kubectl get csv -n openshift-operators aerospike-kubernetes-operator-rhmp.v4.3.0Output Wait for the “PHASE” status to change from
InstallingtoSucceeded:Terminal window NAME DISPLAY VERSION REPLACES PHASEaerospike-kubernetes-operator.v4.3.0 Aerospike Kubernetes Operator 4.3.0 aerospike-kubernetes-operator.v4.0.2 Installingaerospike-kubernetes-operator.v4.3.0 Aerospike Kubernetes Operator 4.3.0 aerospike-kubernetes-operator.v4.0.2 Succeeded
Check AKO logs
AKO runs as two replicas by default for higher availability. Run the following command to follow the logs for the AKO pods.
kubectl -n openshift-operators logs -f deployments/aerospike-operator-controller-manager managerSample output:
2026-01-08T14:27:14Z INFO setup Initializing webhook certificate watcher using provided certificates {"webhook-cert-path": "/tmp/k8s-webhook-server/serving-certs", "webhook-cert-name": "tls.crt", "webhook-cert-key": "tls.key"}2026-01-08T14:27:14Z INFO controller-runtime.certwatcher Updated current TLS certificate2026-01-08T14:27:14Z INFO setup Init aerospike-server config schemas2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "6.0.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "6.1.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "6.2.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "7.0.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "8.0.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "8.1.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "6.3.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "6.4.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "7.1.0"}2026-01-08T14:27:14Z DEBUG setup Config schema added {"version": "7.2.0"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a mutating webhook {"GVK": "asdb.aerospike.com/v1, Kind=AerospikeCluster", "path": "/mutate-asdb-aerospike-com-v1-aerospikecluster"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/mutate-asdb-aerospike-com-v1-aerospikecluster"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a validating webhook {"GVK": "asdb.aerospike.com/v1, Kind=AerospikeCluster", "path": "/validate-asdb-aerospike-com-v1-aerospikecluster"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/validate-asdb-aerospike-com-v1-aerospikecluster"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a mutating webhook {"GVK": "asdb.aerospike.com/v1beta1, Kind=AerospikeBackupService", "path": "/mutate-asdb-aerospike-com-v1beta1-aerospikebackupservice"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/mutate-asdb-aerospike-com-v1beta1-aerospikebackupservice"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a validating webhook {"GVK": "asdb.aerospike.com/v1beta1, Kind=AerospikeBackupService", "path": "/validate-asdb-aerospike-com-v1beta1-aerospikebackupservice"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/validate-asdb-aerospike-com-v1beta1-aerospikebackupservice"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a mutating webhook {"GVK": "asdb.aerospike.com/v1beta1, Kind=AerospikeBackup", "path": "/mutate-asdb-aerospike-com-v1beta1-aerospikebackup"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/mutate-asdb-aerospike-com-v1beta1-aerospikebackup"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a validating webhook {"GVK": "asdb.aerospike.com/v1beta1, Kind=AerospikeBackup", "path": "/validate-asdb-aerospike-com-v1beta1-aerospikebackup"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/validate-asdb-aerospike-com-v1beta1-aerospikebackup"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a mutating webhook {"GVK": "asdb.aerospike.com/v1beta1, Kind=AerospikeRestore", "path": "/mutate-asdb-aerospike-com-v1beta1-aerospikerestore"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/mutate-asdb-aerospike-com-v1beta1-aerospikerestore"}2026-01-08T14:27:14Z INFO controller-runtime.builder Registering a validating webhook {"GVK": "asdb.aerospike.com/v1beta1, Kind=AerospikeRestore", "path": "/validate-asdb-aerospike-com-v1beta1-aerospikerestore"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/validate-asdb-aerospike-com-v1beta1-aerospikerestore"}2026-01-08T14:27:14Z INFO eviction-webhook Eviction webhook metrics registered2026-01-08T14:27:14Z INFO controller-runtime.webhook Registering webhook {"path": "/validate-eviction"}2026-01-08T14:27:14Z INFO setup Adding webhook certificate watcher to manager2026-01-08T14:27:14Z INFO setup Starting manager2026-01-08T14:27:14Z INFO starting server {"name": "health probe", "addr": "[::]:8081"}2026-01-08T14:27:14Z INFO controller-runtime.webhook Starting webhook server2026-01-08T14:27:14Z INFO setup disabling http/22026-01-08T14:27:14Z INFO controller-runtime.webhook Serving webhook server {"host": "", "port": 9443}Grant permissions to the target namespaces
AKO is installed in the openshift-operators namespace.
Grant additional permissions by configuring ServiceAccounts and RoleBindings or ClusterRoleBindings for the target Kubernetes namespace where the Aerospike clusters are created.
You can use the kubectl or akoctl tools to grant permissions for the aerospike namespace.
-
Create the Kubernetes namespace if it doesn’t already exist.
kubectl create namespace aerospike -
Create a service account.
kubectl -n aerospike create serviceaccount aerospike-operator-controller-manager -
Create a RoleBinding or ClusterRoleBinding to attach this service account to the
aerospike-clusterClusterRole. This ClusterRole is created as part of AKO installation and grants Aerospike cluster permissions to the service account.-
For using the Kubernetes native pod-only network to connect to the Aerospike cluster:
-
Create a RoleBinding with the following command:
kubectl -n aerospike create rolebinding aerospike-cluster --clusterrole=aerospike-cluster --serviceaccount=aerospike:aerospike-operator-controller-manager
-
-
For connecting to the Aerospike cluster from outside Kubernetes:
-
Create a ClusterRoleBinding with the following command:
kubectl create clusterrolebinding aerospike-cluster --clusterrole=aerospike-cluster --serviceaccount=aerospike:aerospike-operator-controller-managerAdd multiple
--serviceaccountparameters to the previous command to attach multiple service accounts of different namespaces at one time.Example: To attach service accounts of the aerospike and aerospike1 namespaces:
kubectl create clusterrolebinding aerospike-cluster --clusterrole=aerospike-cluster --serviceaccount=aerospike:aerospike-operator-controller-manager --serviceaccount=aerospike1:aerospike-operator-controller-manager -
If the required ClusterRoleBinding already exists in the cluster, edit it to attach a new service account.
kubectl edit clusterrolebinding aerospike-cluster -
The
kubectl editcommand launches an editor. Append the following lines to thesubjectssection:kind: ServiceAccountname: aerospike-operator-controller-managernamespace: aerospike -
Save and ensure that the changes are applied.
-
-
For instructions on installing the akoctl plugin, see akoctl installation.
-
For using the Kubernetes native pod-only network to connect to the Aerospike cluster, grant namespace scope permissions:
kubectl akoctl auth create -n aerospike --cluster-scope=false -
For connecting to the Aerospike cluster from outside Kubernetes, grant cluster scope permissions:
kubectl akoctl auth create -n aerospikeTo grant permissions for multiple namespaces at the same time, specify a comma-separated namespace list with the
-nflag.kubectl akoctl auth create -n aerospike,aerospike1
OpenShift Security Context Constraints (SCC)
On OpenShift clusters, administrators can use security context constraints (SCCs) to control permissions for pods. These permissions control which actions a pod can perform and which resources it can access. You can use SCCs to define a set of conditions that a pod must run with in order to be accepted into the system. In order to run Aerospike Database Enterprise Edition clusters on OpenShift, the Aerospike pods need to be granted access to some of the cluster SCCs.
The following SCCs are commonly used in most Aerospike deployments. See the OpenShift SCC Guide for additional details.
SCC anyuid (required)
Aerospike Database Enterprise Edition images are designed to run as some non-root (any) UID.
On OpenShift, this requires Aerospike pods to be allowed to run with any UID, requiring the anyuid SCC.
Grant this SCC to the Aerospike cluster service account for the aerospike namespace using the following command:
oc adm policy add-scc-to-user anyuid system:serviceaccount:aerospike:aerospike-operator-controller-managerSCC hostnetwork (optional)
This SCC allows using host networking and host ports.
Grant this SCC to the Aerospike cluster service account for the aerospike namespace using the following command:
oc adm policy add-scc-to-user hostnetwork system:serviceaccount:aerospike:aerospike-operator-controller-managerSCC privileged (optional)
This SCC allows access to all privileged and host features and the ability to run as any user, any group, any FSGroup, and with any SELinux context.
This is required to run Index on Flash storage configuration with Aerospike primary index stored on SSD devices.
Grant this SCC to the Aerospike cluster service account for the aerospike namespace using the following command:
oc adm policy add-scc-to-user privileged system:serviceaccount:aerospike:aerospike-operator-controller-managerNext steps
AKO is now installed and watching the namespaces you configured.
- To deploy your first Aerospike cluster, continue to Create an Aerospike cluster on Kubernetes.
- For a step‑by‑step tutorial including AKO and a sample cluster on GKE or EKS, see Get started with AKO in the cloud.