TLS setup for Aerospike Graph Service
Transport Layer Security (TLS) is a protocol that encrypts data to secure communication over the internet. Aerospike Graph Service (AGS) supports TLS between Gremlin client applications and AGS, as well as between AGS and the underlying Aerospike database.
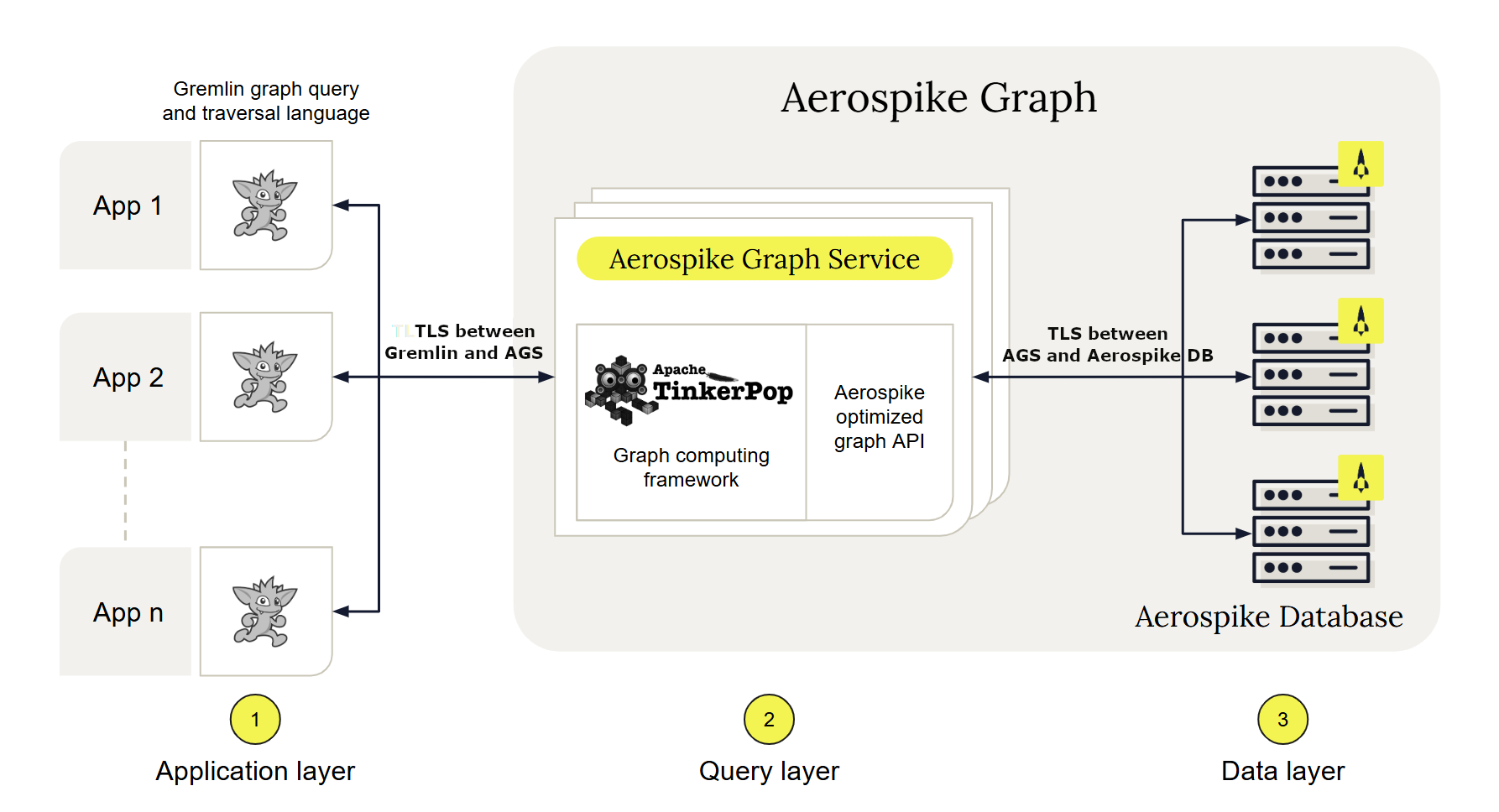
For details on setting up TLS with your AGS deployment, see the following pages: